allanwallace.uk : Security
I don't necessarily agree that all websites should be https enabled, but by the same token I do believe that PII data should be protected in line with GDPR.
In the EU (and alternatively in a post-Brexit UK) we are bound by GDPR, which is quite clear on two points:
• Secure by default
• Secure by design
As with everything in I.T. there are exceptions to every rule however for websites and email the following should be a list of pre-requisites:
• Secure by default
• Secure by design
What does this mean to you?
Whether you are a server administrator, GDPR officer or simply a member of the general public, the following is my opinion based on my understanding of the minimum set of standards that should be adhered to in order attain GDPR compliance.
Why?
• I can be risk-averse - I'd prefer to get this bit right.
• I'd also prefer those handling my PII data to get it right too.
• It's easier for us all to accomplish this if clear guidance is available in one place.
• The smaller your business, the easier this is: Use a professional managed service.
My interpretation of Secure by default and how it affects businesses operating online is as follows:
Email, Email Servers, Email Service.:
• Transmission of emails in plain text is not acceptable for PII data
- it's insecure by default and insecure by design
• The lowest form of permissable* encryption is TLSv1.1
* PCI-DSS "require" TLSv1.1 minimum for a mailserver to be PCI-DSS v3.2.1 compliant.
* There may be an argument for supporting a very restricted set of Ciphers for TLSv1.
• TLSv1.1 must be supported with a restricted set of TLSv1.1 ciphers.
• TLSv1.2 should be supported with a restricted set of TLSv1.2 ciphers
• 100% of outbound emails containing PII data must be sent using TLS.
• 100% of outbound emails must comply with PECR
• 100% of inbound emails should* be received using TLS.
* some email service providers are pretty bad in this area.
• 100% of domains should enable DKIM with strict SPF and strict DMARC policies.
- doing so correctly protects EVERYONE from spoofed emails
- and helps a domain's owner spot spoofing.
Email Server Examples
Two of my SMTP servers tested independently via: https://immuniweb.com/ssl


In other words my two email servers above comply with PCI-DSS* and have "no major issues" in terms of compiance with HIPAA and NIST
The minor HIPAA and NIST compliance issues are because:
postfix does not support OCSP stapling.
On the other hand postfix does support DNSSEC + DANE
- so if you want to secure it beyond OCSP stapling, you can.
As for the email servers themselves, I setup and configured these myself.
It's not difficult to do once you know how to setup postfix securely
Websites:
• All businesses handling PII data on EU citizens should enforce HTTPS with TLSV1.1 and above unless that website simply does HTTP redirection to a https domain.
• The lowest form of permissable* encryption is TLSv1.2
* PCI-DSS "require" TLSv1.1 minimum to be PCI-DSS v3.2.1 compliant.
* There may be an argument for supporting a very restricted set of Ciphers for TLSv1.
• TLSv1.1 should be deprecated.
* There may be an argument for supporting a very restricted set of TLSv1.1 ciphers.
• TLSv1.2 must be supported with a restricted set of TLSv1.2 ciphers
• TLSv1.3 should be supported with a restricted set of TLSv1.2 ciphers
Website Examples
This is my website, there are many like it, but this one is mine:
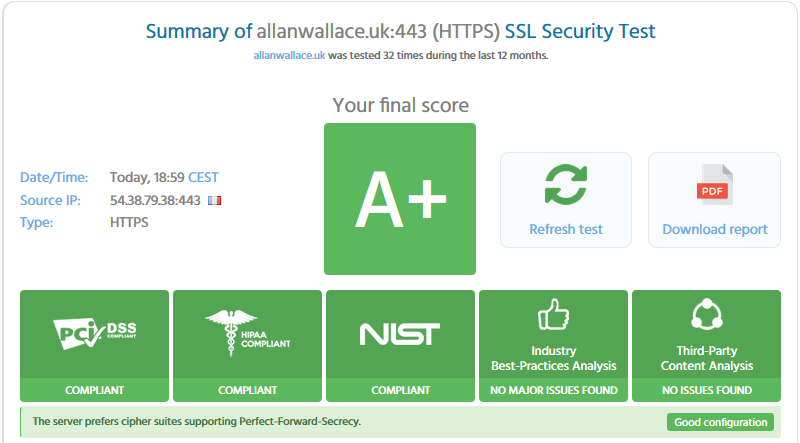
Thank you to https://immuniweb.com/ssl for it's security testing tools.
allanwallace.uk is PCI-DSS, HIPAA & NIST compliant.
This is also my website, there are many like it, but this one is also mine:
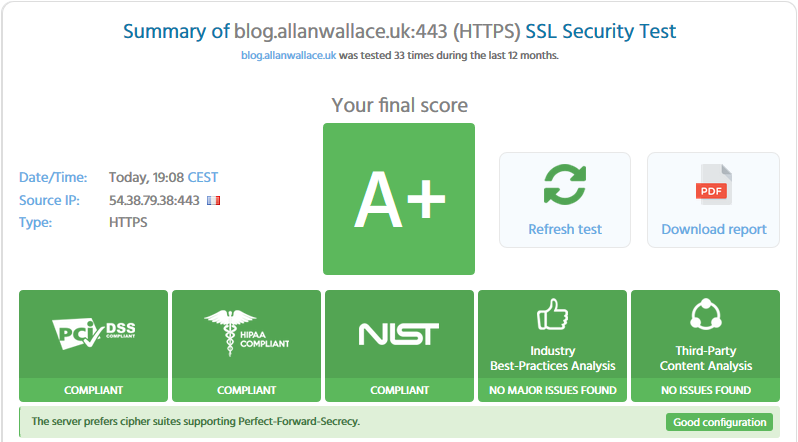
Thank you to https://immuniweb.com/ssl for it's security testing tools.
blog.allanwallace.uk is PCI-DSS, HIPAA & NIST compliant.
If I can do it, other IT professionals should be able to do so for you.
P.S. DNSSEC + DANE may be better than HIPAA + NIST compliance in specific scenarios.
internet.nl's Hall of fame can confirm I try hard to secure my websites
Footnotes:
Are (re)CAPTCHAs on website contact forms a good idea?
There some questioning this in relation to Google at the moment,
and certainly AI has reached a point where the human users are now less accurate at some of these tests than the AI,
but while there are some questioning privacy, I quite like adverts aimed at me to suit my wants.
On the subject of Online Certificate Status Protocol (OCSP) and HIPAA compliance I believe this is an area where compliance can introduce a vulnerability and a privacy issue.
In terms of that vulnerability
it exists where an entity has access to the private keys. If that entity is a state, then you cannot guarantee that the communications are secure.
Living in the United Kingdom of Great Britain & Northern Ireland, I personally have no issue with this.
However, if you are an entity (such as a government body) then ignoring HIPAA compliance and using self-signed certificates with DNSSEC + DANE may be more security conscious for your needs.
My experience with DANE has been that sometimes it's a bit of a pain. More automation required...
To be continued).
In terms of the privacy issue
If your browser is checking the certificate validity against the certificate authority then the certifiate authority may learn which websites you are browsing
- and potentially this may involve what is classed as PII data under GDPR.
I guess some feel similarly about Google's reCaptcha.
Further reading:
NIST SP 800-171 revision 2,
Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
NIST SP 800-172 final draft,
Enhanced Security Requirements for Protecting Controlled Unclassified Information
NIST SP 800 177 revision 1,
Trustworthy Email
From the Dutch NCSC:
IT Security Guidelines for Transport Layer Security
Last Updated 2022/04/12 17:23 CET.
Cookie Policy
Privacy Policy
Security Policy
Terms & Conditions
© 2020 Allan Wallace



